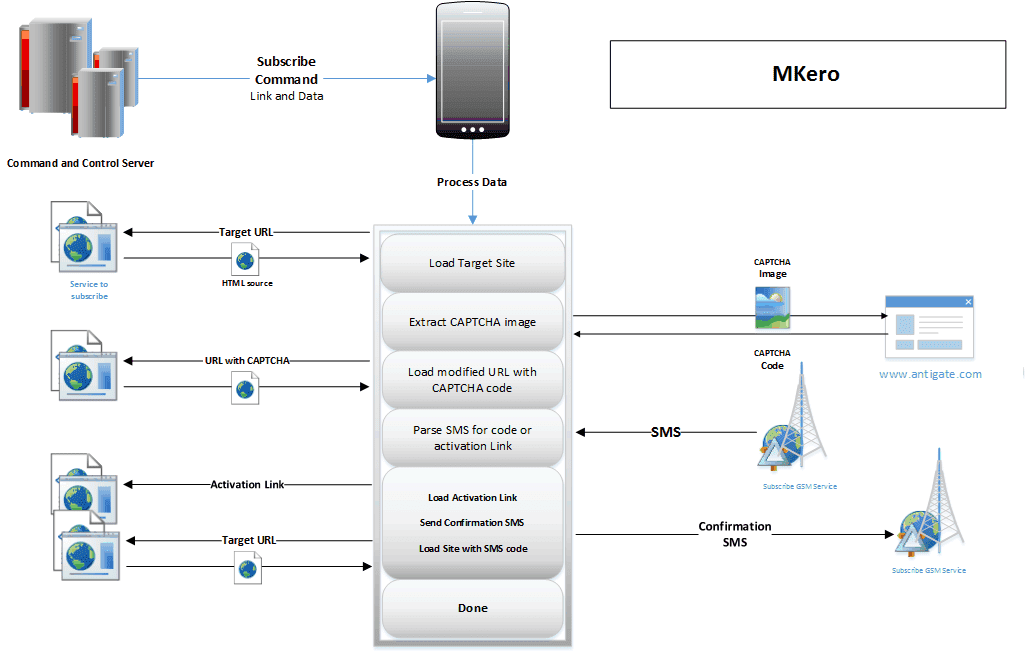
After receiving the sent back request, the Trojan interacts with a command-and-control (C&C) infrastructure which loads the CAPTCHA code on the target link, parses an SMS code for an activation , and ultimately subscribe the user to the premium service.The following Image demonstrates it.
Google Play has been notified of at least seven apps that exhibit this type of behavior, two of which have been downloaded between 100,000 and 500,000 times. Moreover, these seven malware-harboring Google Play applications have been analysed and a list of 29 randomly generated C&C servers names were recovered from a single sample which did not have any encrypted strings. Hence, if any one of these locations became unresponsive –due to a takedown or any other reason – the malware on any infected device will automatically reconnect to the next C&C server in the preconfigured list and proceed with the preset instructions. The total financial losses have been estimated to amount to a staggering $250,000, which is from the minimum $0.50 charged for sending the subscription SMS messages.